
Linux Common Firewall Rules and Commands in iptables
Table of Contents
If you are using Computers for while, you must be familiar with the word “Firewall”. We know that things do seem complex from the surface but through this tutorial, we are going to explain the basis of IPTable and the use of basic commands so that even if you are a networking student or want to deep dive into networks, you can benefit from this guide.
What is firewall ?
A firewall is a network security device that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on a defined set of security rules.

Here we are going to show you some linux common firewall rules and commands in iptables. Iptables is a useful command line utility for configuring Linux kernel firewall. Iptables contains five tables: raw, filter, nat, mangle and security. Each table consist of chains. A chain is a list of firewall rules which are followed in order.
Tables in IPTables
There are 5 types of tables in IPTables and each has different rules applied. So let’s start with the most common table “Filer”.
- Filter Table – This is the default and main table while using IPTables. It means whenever you won’t mention any specific table while applying rules, they will be applied to the filter table. As its name suggests, the role of the Filter table is to decide whether the packages should be allowed to reach their destination or deny their request.
- NAT (Network Address Translation) – As its name suggests, this table allows users to determine the translation of network addresses. The role of this table is to determine whether to modify and how to modify the source and destination of the packet address.
- Mangle Table – This table allows us to modify the IP headers of packets. For example, you can adjust TTL to either lengthening or shorting network hops that the packet can sustain. Similarly, other IP headers can also be modified according to your preference.
- RAW Table – The main use of this table is to track connections as it provides a mechanism for marking packets to view packets as a part of an ongoing session.
- Security Table – Using the Security table, users can apply internal SELinux security context marks on network packets.
For the most use cases, the last 2 types (RAW and Security) of the table don’t have much to do and only the first 3 options are counted as main tables.
Chains in IPTables
They behave at points in the route of the network where we can apply rules. In IPTables, we 5 types of chains and we will discuss each of them. Keep in mind that not each type of chain is available for each type of table.
- Pre-routing – This chain is applied to any incoming packet once it is entered the network stack and this chain is processed even before any routing decision has been made regarding the final destination of the packet.
- Input Chain – It is the point where a packet enters the network stack.
- Forward Chain – It is the point where the packet has been forwarded through your system.
- Output Chain – The output chain is applied to the packet when it originated through your system and goes out.
- Post-routing – This is the complete opposite of the pre-routing chain and is applied to forwarded or outgoing packets once the routing decision has been made.
Now, the only thing left to discuss is rules, and it’s the easiest one out of the 3 that we have discussed here. So let’s complete what’s left on the theoretical part.
Rules in IPTables
Rules are nothing but the set or individual commands by which users manipulate network traffic. Once each chain will come into action, the packet will be checked against defined rules.
If one rule does not satisfy the condition, it will be skipped to the next one and if it satisfies the condition, the next rule will be specified by the value of the target.
each rule has two components: the matching component and the target component.
- Matching Component – They are different conditions to define rules which can be matched by protocol, IP address, port address, interfaces, and headers.
- Target Component – This is an action that will be triggered once the conditions are satisfied.
This was the explanation part and now we will be covering basic commands related to IPTables in Linux.
Let’s get started with some common firewall rules and commands in iptables.
Log in to your Server via SSH as user root


Installing iptables is very easy. If you have an Ubuntu or a Debian , run the following commands:

If there is CentOS installed on your server, run the following commands:

That’s it, now you should have successfully installed iptables on your server.
Now, Lets see the common firewall rules in iptables
Listed below are examples about common firewall rules.
Accept all ESTABLISHED and RELATED packets:

Allow HTTP and HTTPS connections from anywhere:

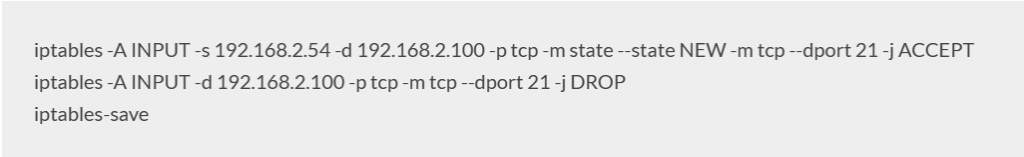
Allow access on port 21 from a specific IP address only (e.g. 192.168.2.54) and block access from all other IPs to the server (e.g. server IP 192.168.2.100) :
Block an IP address (e.g. 192.168.2.74):

Block an IP range and reject all packets (e.g. 192.168.2.0/24):

To block outgoing traffic to a port, (e.g. port 123), use:

Common iptables commands
List all rules in all chains in verbose mode and display the IP addresses and port numbers instead host names and services, including the interface name, the rule options (if any), and the TOS masks:

To display rules in chains with rule numbers, use:

This is useful if you want to delete a rule (e.g. delete rule number 9 from the INPUT chain):

Or, add a rule between two existing rules (e.g. add a firewall rule between rules number 2 and 3):
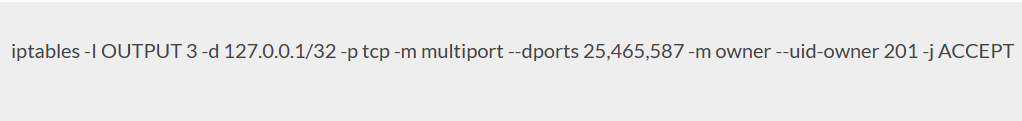
In order to list all commands that were used to create the currently used iptables rules, use the following command:

This command is useful if you need to edit or delete some firewall rules.

Clear all firewall rules:

Use ‘iptables -h | less’ for more information on all iptables command options.
Hope this article helps you, please share your valuable comments to improve us.
